FileBound: SAML NameID Policy Examples
SAML NameID Policy (Okta and ADFS examples)
Your Identity Provider MUST accept Authentication Requests and send Response Assertions with the Subject NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
We do NOT process claims besides the Name ID. We only read the Response Assertion Subject Name ID for an email and compare that to the FileBound user’s email.
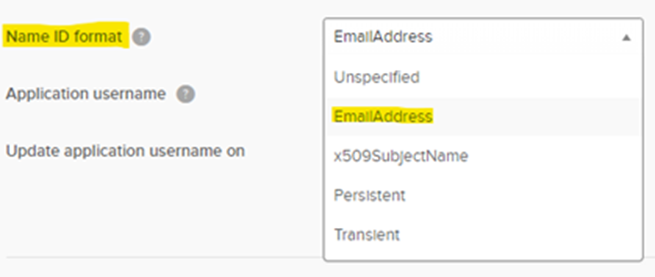
Identity Providers usually have a drop down for Name ID Format.
Okta is very easy:
Whereas ADFS requires (in this order):
- Rule to Send LDAP Attributes as Claims mapping LDAP E-Mail-Address to Outgoing Claim Type E-Mail Address.
- Rule to Transform an Incoming Claim of E-Mail Address to Outgoing claim type: Name ID with an outgoing Name Id format of Email.
